Multi-Account + Proxy Setup
Running a single Telegram account for outreach is like shipping all traffic through one tiny gateway: it throttles scale and draws unwanted attention. A multi-account + proxy architecture solves both problems by isolating risk, distributing load, and keeping behavior patterns human. This guide gives you a production-ready plan for 2025—covering proxy selection, safe rotation, warm-up, anti-ban tactics, and day-2 operations. Whenever you need an all-in-one stack, our Telegram automation software supports unlimited accounts, proxy control, randomized delays, and rich telemetry.
The goal of a multi-account setup
- Isolation: Each account operates in its own network and device context.
- Safety at scale: Rotation and randomization keep patterns natural.
- Observability: You can detect anomalies early and pause risky cohorts.
- Replaceability: A flagged account doesn’t take your whole system down.
Reference architecture
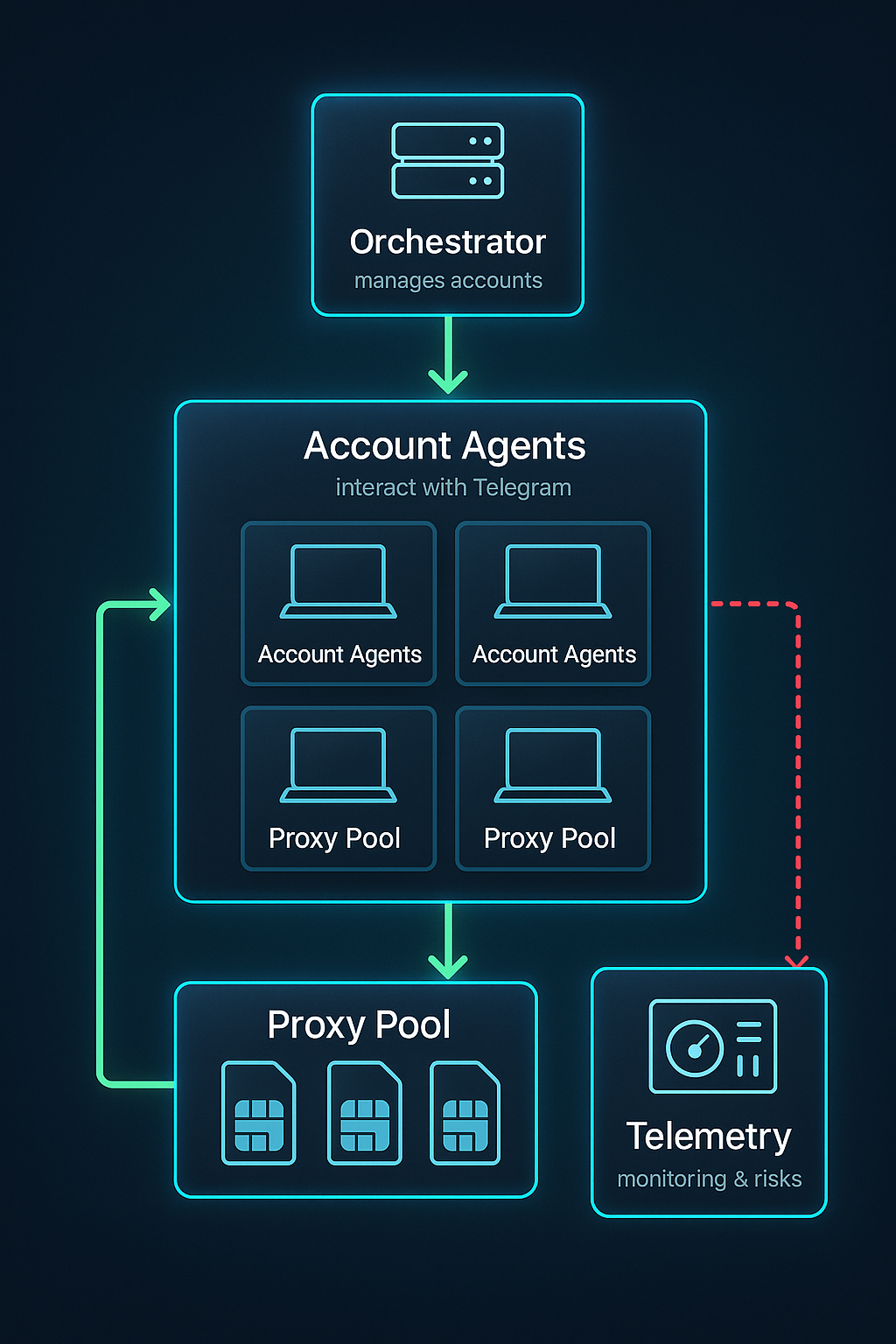
Key components
- Orchestrator: a scheduler that assigns jobs to account agents, enforces pacing, and manages retries.
- Account agents: one container (or process namespace) per account, with its own session files and rate limits.
- Proxy service: handles IP leasing, health checks, rotation policies, and “sticky” assignments.
- Telemetry + alerting: streams per-account metrics like send rate, reply rate, error types, and spam signals.
Step-by-step setup
1) Prepare accounts
- Choose the mix: Use a blend of aged and fresh accounts. Aged accounts tolerate higher caps; fresh accounts require patient warm-up.
- Session storage: Keep each account’s TDATA or SESSION+JSON in a separate folder or volume. Back up encrypted.
- Profile hygiene: Photo, short bio, natural username. Add a handful of groups or channels before any outreach.
- Inventory sheet: Track phone, session path, proxy ID, first-use date, and risk notes.
2) Proxy selection (telegram proxy setup)
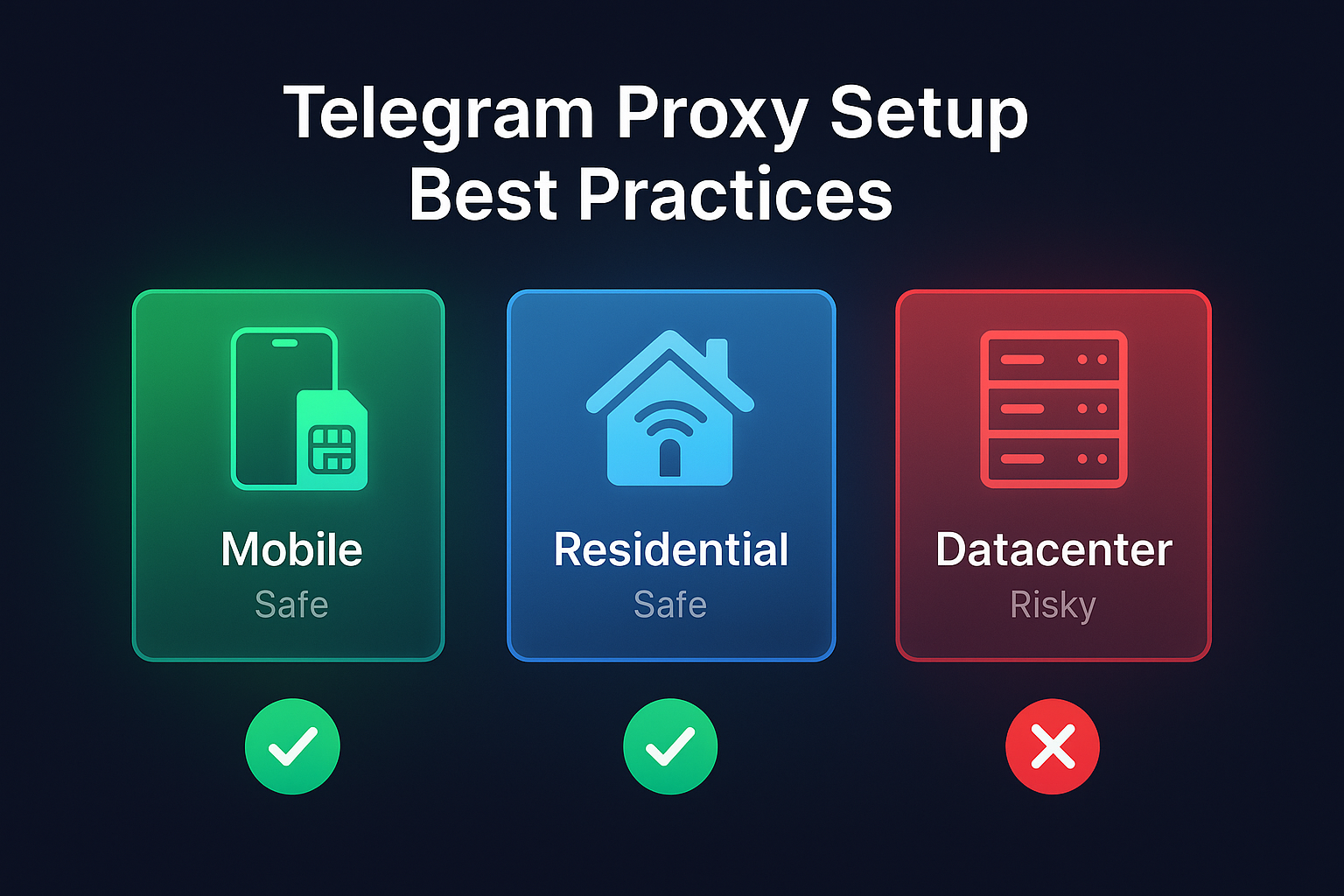
- Types: Prefer mobile or residential. Datacenter proxies are high-risk for scaled outreach.
- Allocation strategy: 1 IP ⇢ 1 account for best safety. Budget mode: 2–3 accounts per IP with stricter pacing.
- Rotation period: Rotate by time (e.g., every 12–24h) or by workload (e.g., every N messages). Keep a sticky window for session stability.
- Health checks: DNS + TLS handshake, latency targets (<250ms), and success rate > 98% on test pings.
3) Containerize account agents
- One agent per account: Easier to isolate logs, CPU/memory, and restarts. Mount session files as read/write volumes.
- Proxy env: Inject proxy creds via environment variables or per-account config files.
- Crash policy: Auto-restart with exponential backoff; alert after N failures in T minutes.
4) Warm-up schedule
Warm-up builds trust. Below is a conservative baseline that adapts to aged vs fresh accounts. Track replies and negative signals to decide whether to pause or progress.
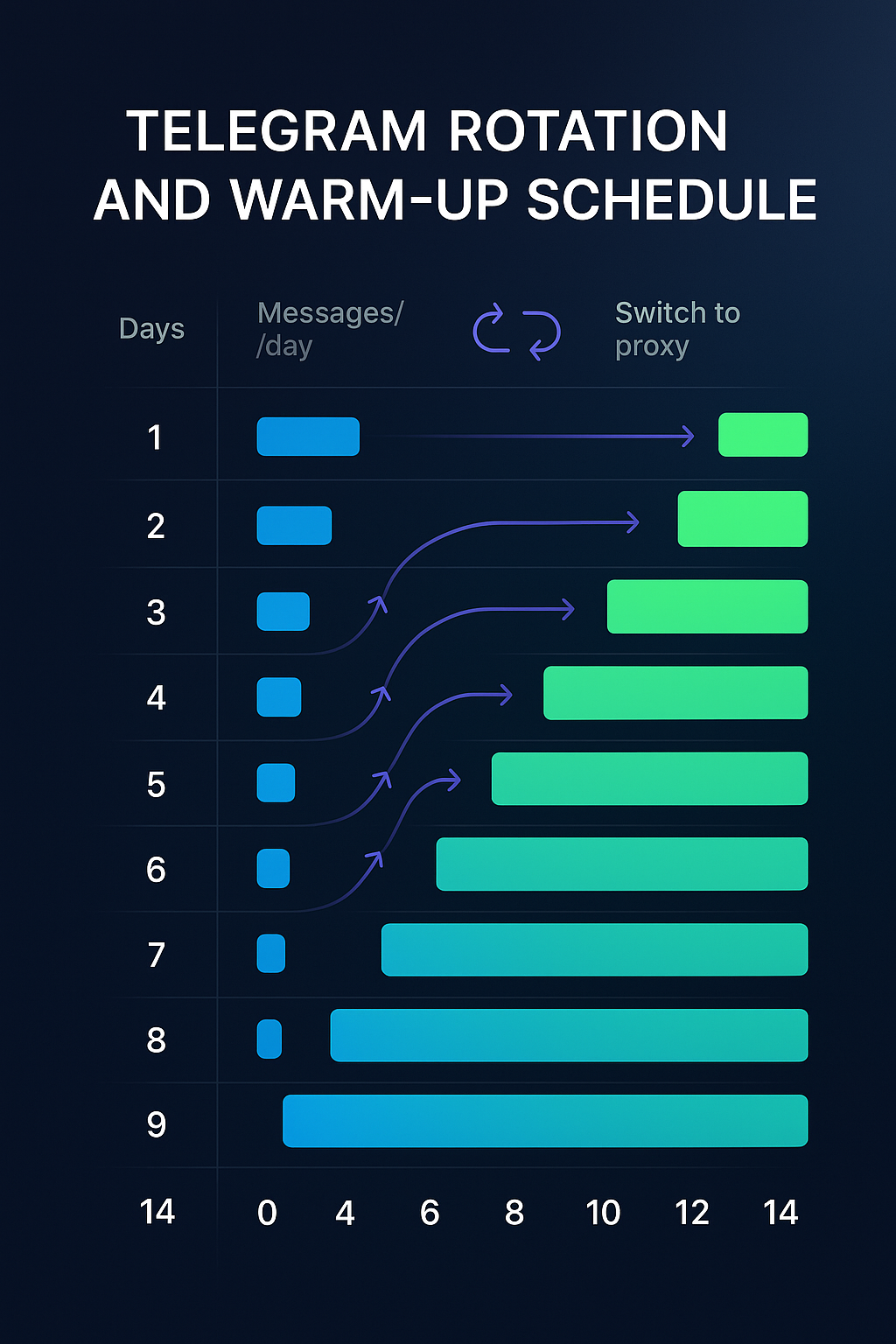
5) Rotation (telegram account rotation)
Rotation is about distribution and natural variance. Two layers matter:
- Account rotation: Distribute daily sends across many accounts; prefer “healthiest” accounts for heavy lifting.
- Proxy rotation: Keep sessions sticky for hours, then rotate on schedule or after N messages.
Rules of thumb: Pause any account with an error spike (>5% within 1 hour) or when replies turn sharply negative. Rotate it out and assign its quota to a healthier peer.
6) Anti-ban practices (anti-ban telegram setup)
- Human pacing: Randomized delays, varied send windows (e.g., split AM/PM), and short “typing” intervals.
- Message diversity: 3–5 copy variants per offer; rotate openers, synonyms, and CTA phrasing.
- Single CTA: One link or one ask. Multiple links look spammy and hurt replies.
- Cohort control: Segment targets by group and recency; never hit the same user twice in a cycle.
- Opt-out hygiene: Tag negative replies and suppress permanently.
Telemetry that actually helps
- Delivery & error rates by account and by proxy.
- Reply % by message template and cohort.
- Time-to-first-reply as a quality proxy for copy + targeting.
- Flag signals (sudden send fails, captcha/lock events) to trigger auto-quarantine.
Our software exposes these as per-account dashboards and JSON exports so you can automate stop/go decisions.
Operational checklists
Preflight (daily)
- Proxy pool health ≥ 98% pass on handshake + latency checks.
- All agents online; no crash loops in the last 12 hours.
- Warm-up vs. production cohorts separated; caps loaded correctly.
- Templates rotated and AB test weights updated.
During send
- Watch per-account error rate; auto-pause at threshold.
- Check reply rate every 200 sends; rebalance towards winners.
- Throttle temporarily if anomaly score increases (e.g., sudden failures across a subnet).
Post-campaign
- Tag leads by template + cohort; push to CRM or spreadsheet.
- Debrief: top 3 learnings on copy, target, timing.
- Archive logs; rotate API keys; refresh a portion of proxies.
Copy patterns that earn replies
Keep it short, context-aware, and easy to say “yes” to. Here are three lightweight templates you can adapt:
- Mutual context: “Saw your post in {group}. If {benefit} is on your roadmap, we built a tiny tool that does {outcome}. Want a 90‑sec preview?”
- Micro-invite: “We host a weekly Q&A for {audience}. No spam, just real playbooks. Want an invite link?”
- Time saver: “Quick one — we cut {task} time by ~40% for teams like {peer}. Worth a 10‑min walkthrough?”
Common mistakes (and quick fixes)
- Too fast, too soon: New accounts sending links on day 1.
- One IP for everything: Cross-contamination; use dedicated/sticky assignments.
- Copy clones: One unchanging message across thousands of users.
- No cohort hygiene: Recontacting the same users; skipping opt-outs.
- Blind to signals: Not monitoring reply trends and error spikes.
Resources & next steps
- Software: Telegram automation software (unlimited accounts, proxy support, random delays, lifetime updates).
- Accounts: High-quality Telegram accounts (TDATA / SESSION+JSON, bulk stock, replacement policy).
- FAQ: Common questions about safety and deliverability → FAQ.
 Telegram Solutions
Telegram Solutions